They are the keys to your digital castle, yet so many use the same password everywhere, or at least variations of it. With so much of life now online, what should you do to protect yourself?
Vox explain the problem rather well.
It is vital to protect your passwords to prevent problems; firefighting them is a big headache to say the least! Here are our suggestions to improve your digital security.
Contents
Use a good password manager
There are many out there, so make sure you find one that’s right for you. Here are some suggestions.
LastPass
This cloud service is free if you only need to use either mobile or desktop devices. If you want to use both types, it will cost you £30 per year, though a six-person family account is just £40.80 per year – that’s about 56p per person per month. Used by pretty much every IT department ever.
KeyPass
This is a self-hosted and open source option. You will need to keep your password database safe yourself, but the upside is that you can lock it down as much as you like, so you could physically prevent access to it if you wanted to.
Dashlane
Another cloud offering, this one is often found sponsoring your favourite YouTuber.
Make your passwords long. Really long.
IT guys used to recommend making your password complex by including lots of different types of characters. Turns out that this is not correct; the best thing to do is make your password super long. This is because every character you add increases the potential combinations exponentially. Using a “bruit force” attack, one where the cracker just tries every combination, more combinations means more time and more time means harder to crack.
For example, just for the sake of example say you used just the 26 lowercase English characters in your password. Obviously don’t do that, but it’s just a simple example. Here is the number of possibilities for each character length.
| Number of Characters in Password | Possible Permutations |
| 1 | 26 |
| 2 | 676 |
| 3 | 17,576 |
| 4 | 456,976 |
| 5 | 11,881,376 |
| 6 | 308,915,776 |
| 7 | 8,031,810,176 |
| 8 | 208,827,064,576 |
| 9 | 5,429,503,678,976 |
| 10 | 141,167,095,653,376 |
As you can see, the number of permutations rapidly increases as you add more characters. Here is the same data, but extended to a length of 50 characters.
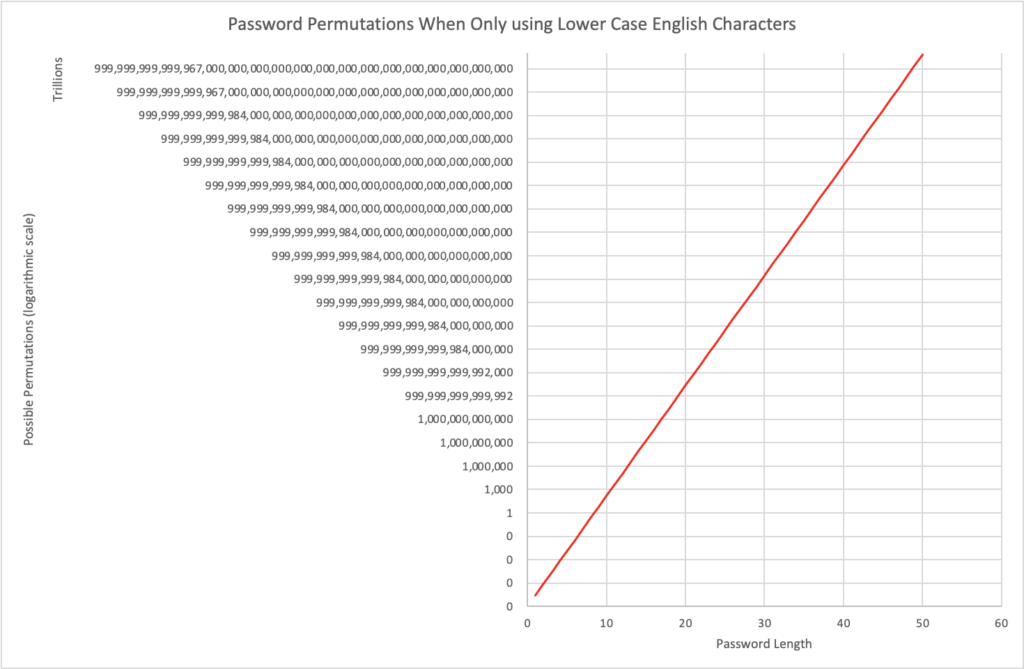
This graph is shown in a logarithmic scale and in trillions on the vertical axis, as the numbers get extremely large, extremely quickly; and that’s only using lower case English characters! Your computer is capable of recording a total of 143,859 characters, so a 100 character password that potentially any of them could take three hundred quadrillion quinquagintillion years to crack! Just to put that into perspective,
Our galaxy is likely to [end] within the next 5 billion years.
Cornell University, “Eternal inflation predicts that time will end“, 2010-09
Very long passwords will probably take more time to crack than you, or the universe, will live! This is why the UK National Cyber Security Centre now recommends avoiding complexity and maximum length requirements, but also setting a minimum length.
Using complexity requirements is a poor defence against guessing attacks.
You should specify a minimum password length, to prevent very short passwords.
Password length should only be capped by the capabilities of your system.
UK NCSC, “Password administration for system owners – Password policy: updating your approach“, 2019-11
Make every password entirely unique
I have spoken to people who say “I have a system to remember my passwords, so I don’t need a password manager.” This usually means that most of their passwords are broadly the same, because the human brain is pants at creating randomness, let alone remembering it.
The importance of unique passwords cannot be overstated. For example, say you registered at BobsCurtains.example.com. Bob is (hypothetically) a lovely chap who sells great curtains, but he’s not an InfoSec expert, so his website is not the most secure on the planet. You then register on Facebook with the same password. What harm could that do?
What could happen, and often does, is that a nasty person finds a security vulnerability at BobsCurtains.example.com and silently starts downloading all user data, including your email address and password. Many such intrusions remain active for many months without detection, so the small business owner might never know.
The nasty cracker would then try your credentials at every major website, such as facebook. Once they have access to your facebook, they not only have access to post nasty things in your name, but also every site that you have used “Log in with facebook” at.
This is clearly just one example, but as mentioned most people use the same password everywhere, so potentially all your accounts could be at risk. No, variations on a theme do not help, as password cracking software is smart enough to try all the similar passwords too.
Get your password manager to create a unique password every time.
Use MFA
Multi Factor Authentication, also known as MFA for short, requires that you use more than one method to prove that you are really you. You will also see the term Two Factor Authentication used widely, also known as 2FA, though this is specifically using two out of the possible three factors.
Tom Scott explains this well.
Get a YubiKey
Preferably two YubiKeys.
This is technically part of the MFA, but takes things one step further. I could give you my Facebook password (I won’t, don’t get your hopes up) but you would still be unable to get in because you don’t have my physical YubiKey. Passwords can be leaked, even your one-time-password app could potentially be compromised, but your YubiKey is a physical thing that uses hardware encryption. Without physical access to that physical object, the likelihood of your account being compromised is reduced significantly.
The best practice YubiKey use is to purchase two; one for every day use and one to put in a safe place, such as a home safe or a safety deposit box. Make sure it is an actual safe place, not just a “safe place” that you will forget about in six weeks. That way, if you lose one, you still have access to all your accounts. Ideally you would never lose your YubiKey, but if you do, this means that you can get into your accounts quickly and disable the lost key.
A YubiKey costs about £40, so two would cost about £80. Yes, this is not exactly cheap, but it is a one-time cost that could prevent you from losing significantly more than £80.
Follow the Yubico quiz to find out which YubiKey is right for you. Better yet, if you buy yours via Geek.Zone/Amazon, Amazon will donate to Geek.Zone with absolutely no cost to you!
Avoid SMS MFA like the Plague
The security of an SMS message, also known as a text message, is reliant on the customer service agent at your mobile phone provider. If you are lucky, every single person who works for your network will be a cynical Cyber Security expert. If you live in the real world, that will not be the case, so most will be swayed by social engineering.
Use a different email address for vital accounts
If you have done all of the above and want to take an extra step, using an email address just for your critical accounts can further help to thwart potential attacks. You would not use this address for general communication and would set up all the security measures that have been discussed above.
For example, these accounts might include,
- Financial institutions
- Mobile telephone providers
- Password manager
You might have other accounts that you consider critical, so take some time to consider which ones would cause most damage to your life if they were compromised. If you want to be extra secure, all your critical accounts would have a different email address and each email address would not be outwardly identifiable as belonging to you.